Zimbra acme.sh SSL 憑證
使用 Let's Encrypt 來產生信任憑證,這個憑證是三個月期限
110.11.08 本篇會修改一下更換新的憑證方式,因之前所跟換的根目錄憑證已經失效無法再使用了及新系統的運行的環境。
運行環境
Ubuntu 18.04 LTS(LXC)、CentOS 7、Zimbra-8.8.15
首先安裝 acme.sh 服務
- 此服務請參考本站之前所設定的方式 acme.sh + Cloudflare 自動更新 Let's Encrypt 服務
由於我是使用萬用憑證方式來進行各站台更換憑證,因此如果您有多台服務的話可以用萬用憑證方式來進行 Zimbra 服務來更新。
- 設定 mail 的腳本,在
/opt目錄下建立產生出來的憑證資料夾ssl,由於 Zimbra 可以多網域在同一台主機上,那憑證可以集合成一張,那如果您只有一個網域,只要設定一組就可以了
export CF_Key="Your_CloudFlare_API_Key"
export CF_Email="[email protected]"
DOMAIN1=網域1
DOMAIN2=網域2
/root/.acme.sh/acme.sh --issue --dns dns_cf --dnssleep 90 -d "mail.${DOMAIN1}" -d "imap.${DOMAIN1}" -d "smtp.${DOMAIN1}" -d "pop.${DOMAIN1}" -d "mail.${DOMAIN2}" -d "imap.${DOMAIN2}" -d "smtp.${DOMAIN2}" -d "pop.${DOMAIN2}" --log \
--cert-file /opt/ssl/cert.pem \
--key-file /opt/ssl/privkey.pem \
--fullchain-file /opt/ssl/fullchain.pem \
--ca-file /opt/ssl/chain.pem
110.11.08 如果您有使用到 Let's Encrypt 服務的話那建議要在 acme.sh 先設定憑證根因為原 Let's Encrypt 所以使用的根憑證已經在 2021.09.30 已到期,那現在官方有在放出最新版本的根憑證。
- 以下是在
.acme.sh環境上指定要有ISRG這個憑證。
./acme.sh --set-default-ca --server letsencrypt
./acme.sh --set-default-chain --preferred-chain ISRG --server letsencrypt
建立中間憑證及 CA 根憑證
由於 Let's Encrypt 產生出來的憑證不包含 CA 根憑證,所以需要使用到 ISRG Root X1 根憑證並且增加到 fullchain.pem 後面,ISRG Root X1 根憑證網址
再將剛剛複製下來的憑證內容增加到 fullchain.pem,範例如下:
-----BEGIN CERTIFICATE-----
您的fullchain內容
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFazCCA1OgAwIBAgIRAIIQz7DSQONZRGPgu2OCiwAwDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
cmNoIEdyb3VwMRUwEwYDVQQDEwxJU1JHIFJvb3QgWDEwHhcNMTUwNjA0MTEwNDM4
WhcNMzUwNjA0MTEwNDM4WjBPMQswCQYDVQQGEwJVUzEpMCcGA1UEChMgSW50ZXJu
ZXQgU2VjdXJpdHkgUmVzZWFyY2ggR3JvdXAxFTATBgNVBAMTDElTUkcgUm9vdCBY
MTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK3oJHP0FDfzm54rVygc
h77ct984kIxuPOZXoHj3dcKi/vVqbvYATyjb3miGbESTtrFj/RQSa78f0uoxmyF+
0TM8ukj13Xnfs7j/EvEhmkvBioZxaUpmZmyPfjxwv60pIgbz5MDmgK7iS4+3mX6U
A5/TR5d8mUgjU+g4rk8Kb4Mu0UlXjIB0ttov0DiNewNwIRt18jA8+o+u3dpjq+sW
T8KOEUt+zwvo/7V3LvSye0rgTBIlDHCNAymg4VMk7BPZ7hm/ELNKjD+Jo2FR3qyH
B5T0Y3HsLuJvW5iB4YlcNHlsdu87kGJ55tukmi8mxdAQ4Q7e2RCOFvu396j3x+UC
B5iPNgiV5+I3lg02dZ77DnKxHZu8A/lJBdiB3QW0KtZB6awBdpUKD9jf1b0SHzUv
KBds0pjBqAlkd25HN7rOrFleaJ1/ctaJxQZBKT5ZPt0m9STJEadao0xAH0ahmbWn
OlFuhjuefXKnEgV4We0+UXgVCwOPjdAvBbI+e0ocS3MFEvzG6uBQE3xDk3SzynTn
jh8BCNAw1FtxNrQHusEwMFxIt4I7mKZ9YIqioymCzLq9gwQbooMDQaHWBfEbwrbw
qHyGO0aoSCqI3Haadr8faqU9GY/rOPNk3sgrDQoo//fb4hVC1CLQJ13hef4Y53CI
rU7m2Ys6xt0nUW7/vGT1M0NPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNV
HRMBAf8EBTADAQH/MB0GA1UdDgQWBBR5tFnme7bl5AFzgAiIyBpY9umbbjANBgkq
hkiG9w0BAQsFAAOCAgEAVR9YqbyyqFDQDLHYGmkgJykIrGF1XIpu+ILlaS/V9lZL
ubhzEFnTIZd+50xx+7LSYK05qAvqFyFWhfFQDlnrzuBZ6brJFe+GnY+EgPbk6ZGQ
3BebYhtF8GaV0nxvwuo77x/Py9auJ/GpsMiu/X1+mvoiBOv/2X/qkSsisRcOj/KK
NFtY2PwByVS5uCbMiogziUwthDyC3+6WVwW6LLv3xLfHTjuCvjHIInNzktHCgKQ5
ORAzI4JMPJ+GslWYHb4phowim57iaztXOoJwTdwJx4nLCgdNbOhdjsnvzqvHu7Ur
TkXWStAmzOVyyghqpZXjFaH3pO3JLF+l+/+sKAIuvtd7u+Nxe5AW0wdeRlN8NwdC
jNPElpzVmbUq4JUagEiuTDkHzsxHpFKVK7q4+63SM1N95R1NbdWhscdCb+ZAJzVc
oyi3B43njTOQ5yOf+1CceWxG1bQVs5ZufpsMljq4Ui0/1lvh+wjChP4kqKOJ2qxq
4RgqsahDYVvTH9w7jXbyLeiNdd8XM2w9U/t7y0Ff/9yi0GE44Za4rF2LN9d11TPA
mRGunUHBcnWEvgJBQl9nJEiU0Zsnvgc/ubhPgXRR4Xq37Z0j4r7g1SgEEzwxA57d
emyPxgcYxn/eR44/KJ4EBs+lVDR3veyJm+kXQ99b21/+jh5Xos1AnX5iItreGCc=
-----END CERTIFICATE-----
驗證您的憑證
- 將剛剛所產生的憑證都複製到
zimbra目錄下
mkdir /opt/zimbra/ssl/letsencrypt
cp /opt/ssl/* /opt/zimbra/ssl/letsencrypt/
chown -R zimbra:zimbra /opt/zimbra/ssl/letsencrypt
ls -l /opt/zimbra/ssl/letsencrypt/
-rw-r--r-- 1 zimbra zimbra 2106 12月 31 14:23 cert.pem
-rw-r--r-- 1 zimbra zimbra 2847 12月 31 14:23 chain.pem
-rw-r--r-- 1 zimbra zimbra 3754 12月 31 14:23 fullchain.pem
-rw------- 1 zimbra zimbra 1679 12月 31 14:23 privkey.pem
- 切換到
zimbra使用者帳號
cd /opt/zimbra/ssl/letsencrypt/
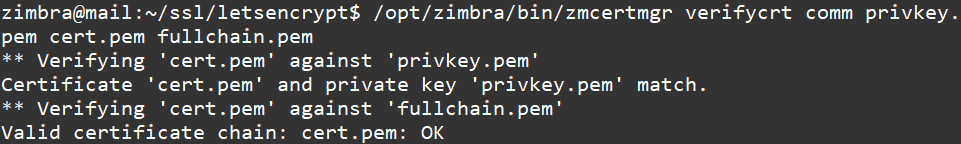
/opt/zimbra/bin/zmcertmgr verifycrt comm privkey.pem cert.pem fullchain.pem
- 結果如下,看到最後有顯示 ok 表示此憑證是可以使用的
部署憑證
- 備份憑證
cp -a /opt/zimbra/ssl/zimbra /opt/zimbra/ssl/zimbra.$(date "+%Y%m%d")
- 執行結果
drwxr-xr-x 2 zimbra zimbra 4096 12月 31 14:23 letsencrypt
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra.20191230153933
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra.20191230153936
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra.20191230153939
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra.20191230153941
drwxr-x--- 5 zimbra zimbra 4096 12月 30 15:39 zimbra.20191231 << 這是剛剛建立的目錄
- 將憑證複製到
Zimbra認識憑證目錄下
cp /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
- 切換到
zimbra使用者帳號進行部署
su zimbra
cd letsencrypt/
/opt/zimbra/bin/zmcertmgr deploycrt comm cert.pem chain.pem
- 執行結果如下
** Fixing newlines in 'chain.pem'
Can't rename chain.pem to chain.pem.bak: 拒絕不符權限的操作, skipping file at /opt/zimbra/bin/zmcertmgr line 1239.
** Verifying 'cert.pem' against '/opt/zimbra/ssl/zimbra/commercial/commercial.key'
Certificate 'cert.pem' and private key '/opt/zimbra/ssl/zimbra/commercial/commercial.key' match.
** Verifying 'cert.pem' against 'chain.pem'
Valid certificate chain: cert.pem: OK
** Copying 'cert.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Copying 'chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt'
** Appending ca chain 'chain.pem' to '/opt/zimbra/ssl/zimbra/commercial/commercial.crt'
** Importing cert '/opt/zimbra/ssl/zimbra/commercial/commercial_ca.crt' as 'zcs-user-commercial_ca' into cacerts '/opt/zimbra/common/lib/jvm/java/lib/security/cacerts'
** NOTE: restart mailboxd to use the imported certificate.
** Saving config key 'zimbraSSLCertificate' via zmprov modifyServer mail.freedomstu.com...ok
** Saving config key 'zimbraSSLPrivateKey' via zmprov modifyServer mail.freedomstu.com...ok
** Installing imapd certificate '/opt/zimbra/conf/imapd.crt' and key '/opt/zimbra/conf/imapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/imapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/imapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/conf/imapd.keystore'
** Installing ldap certificate '/opt/zimbra/conf/slapd.crt' and key '/opt/zimbra/conf/slapd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/slapd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/slapd.key'
** Creating file '/opt/zimbra/ssl/zimbra/jetty.pkcs12'
** Creating keystore '/opt/zimbra/mailboxd/etc/keystore'
** Installing mta certificate '/opt/zimbra/conf/smtpd.crt' and key '/opt/zimbra/conf/smtpd.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/smtpd.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/smtpd.key'
** Installing proxy certificate '/opt/zimbra/conf/nginx.crt' and key '/opt/zimbra/conf/nginx.key'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.crt' to '/opt/zimbra/conf/nginx.crt'
** Copying '/opt/zimbra/ssl/zimbra/commercial/commercial.key' to '/opt/zimbra/conf/nginx.key'
** NOTE: restart services to use the new certificates.
** Cleaning up 3 files from '/opt/zimbra/conf/ca'
** Removing /opt/zimbra/conf/ca/2eecd714.0
** Removing /opt/zimbra/conf/ca/ca.key
** Removing /opt/zimbra/conf/ca/ca.pem
** Copying CA to /opt/zimbra/conf/ca
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.key' to '/opt/zimbra/conf/ca/ca.key'
** Copying '/opt/zimbra/ssl/zimbra/ca/ca.pem' to '/opt/zimbra/conf/ca/ca.pem'
** Creating CA hash symlink '2eecd714.0' -> 'ca.pem'
** Creating /opt/zimbra/conf/ca/commercial_ca_1.crt
** Creating CA hash symlink '4f06f81d.0' -> 'commercial_ca_1.crt'
** Creating /opt/zimbra/conf/ca/commercial_ca_2.crt
** Creating CA hash symlink '2e5ac55d.0' -> 'commercial_ca_2.crt'
- 重啟
zimbra服務,開啟網頁連線看看憑證是否已生效。
zmcontrol restart
自動更新憑證及重啟服務
腳本給大家參考,在利用二個月排程方式來進行腳本
#!/bin/bash
#source /etc/profile
# Others vars
BACK_DIR="/opt/ssl" # 要備份到目錄
DATE_TITILE=$(date +%F) # 標題時間
DATE_TODAY=$(date +%F-%H%M%S) # 備份時間
# 如果該目錄不存在則建立新目錄
if [ ! -d $BACK_DIR ]; then
mkdir -p $BACK_DIR
fi
# 進到備份目錄
cd $BACK_DIR
echo "-----$DATE_TITILE-----" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
echo "寫入 fullchain.pem 檔" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
echo '''-----BEGIN CERTIFICATE-----
MIIFazCCA1OgAwIBAgIRAIIQz7DSQONZRGPgu2OCiwAwDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
cmNoIEdyb3VwMRUwEwYDVQQDEwxJU1JHIFJvb3QgWDEwHhcNMTUwNjA0MTEwNDM4
WhcNMzUwNjA0MTEwNDM4WjBPMQswCQYDVQQGEwJVUzEpMCcGA1UEChMgSW50ZXJu
ZXQgU2VjdXJpdHkgUmVzZWFyY2ggR3JvdXAxFTATBgNVBAMTDElTUkcgUm9vdCBY
MTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK3oJHP0FDfzm54rVygc
h77ct984kIxuPOZXoHj3dcKi/vVqbvYATyjb3miGbESTtrFj/RQSa78f0uoxmyF+
0TM8ukj13Xnfs7j/EvEhmkvBioZxaUpmZmyPfjxwv60pIgbz5MDmgK7iS4+3mX6U
A5/TR5d8mUgjU+g4rk8Kb4Mu0UlXjIB0ttov0DiNewNwIRt18jA8+o+u3dpjq+sW
T8KOEUt+zwvo/7V3LvSye0rgTBIlDHCNAymg4VMk7BPZ7hm/ELNKjD+Jo2FR3qyH
B5T0Y3HsLuJvW5iB4YlcNHlsdu87kGJ55tukmi8mxdAQ4Q7e2RCOFvu396j3x+UC
B5iPNgiV5+I3lg02dZ77DnKxHZu8A/lJBdiB3QW0KtZB6awBdpUKD9jf1b0SHzUv
KBds0pjBqAlkd25HN7rOrFleaJ1/ctaJxQZBKT5ZPt0m9STJEadao0xAH0ahmbWn
OlFuhjuefXKnEgV4We0+UXgVCwOPjdAvBbI+e0ocS3MFEvzG6uBQE3xDk3SzynTn
jh8BCNAw1FtxNrQHusEwMFxIt4I7mKZ9YIqioymCzLq9gwQbooMDQaHWBfEbwrbw
qHyGO0aoSCqI3Haadr8faqU9GY/rOPNk3sgrDQoo//fb4hVC1CLQJ13hef4Y53CI
rU7m2Ys6xt0nUW7/vGT1M0NPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNV
HRMBAf8EBTADAQH/MB0GA1UdDgQWBBR5tFnme7bl5AFzgAiIyBpY9umbbjANBgkq
hkiG9w0BAQsFAAOCAgEAVR9YqbyyqFDQDLHYGmkgJykIrGF1XIpu+ILlaS/V9lZL
ubhzEFnTIZd+50xx+7LSYK05qAvqFyFWhfFQDlnrzuBZ6brJFe+GnY+EgPbk6ZGQ
3BebYhtF8GaV0nxvwuo77x/Py9auJ/GpsMiu/X1+mvoiBOv/2X/qkSsisRcOj/KK
NFtY2PwByVS5uCbMiogziUwthDyC3+6WVwW6LLv3xLfHTjuCvjHIInNzktHCgKQ5
ORAzI4JMPJ+GslWYHb4phowim57iaztXOoJwTdwJx4nLCgdNbOhdjsnvzqvHu7Ur
TkXWStAmzOVyyghqpZXjFaH3pO3JLF+l+/+sKAIuvtd7u+Nxe5AW0wdeRlN8NwdC
jNPElpzVmbUq4JUagEiuTDkHzsxHpFKVK7q4+63SM1N95R1NbdWhscdCb+ZAJzVc
oyi3B43njTOQ5yOf+1CceWxG1bQVs5ZufpsMljq4Ui0/1lvh+wjChP4kqKOJ2qxq
4RgqsahDYVvTH9w7jXbyLeiNdd8XM2w9U/t7y0Ff/9yi0GE44Za4rF2LN9d11TPA
mRGunUHBcnWEvgJBQl9nJEiU0Zsnvgc/ubhPgXRR4Xq37Z0j4r7g1SgEEzwxA57d
emyPxgcYxn/eR44/KJ4EBs+lVDR3veyJm+kXQ99b21/+jh5Xos1AnX5iItreGCc=
-----END CERTIFICATE-----''' >> $BACK_DIR/fullchain.pem
echo "在 zimbra 建立新目錄並且複製" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
if [ ! -d /opt/zimbra/ssl/letsencrypt ]; then
mkdir /opt/zimbra/ssl/letsencrypt
fi
cp /opt/ssl/* /opt/zimbra/ssl/letsencrypt/
chown -R zimbra:zimbra /opt/zimbra/ssl/letsencrypt
echo "進入剛剛建立的目錄" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
cd /opt/zimbra/ssl/letsencrypt/
echo "切換成 zimbra 驗證看是否正常" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
su zimbra -c '/opt/zimbra/bin/zmcertmgr verifycrt comm privkey.pem cert.pem fullchain.pem' >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
echo "備份憑證" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
su zimbra -c 'cp -a /opt/zimbra/ssl/zimbra /opt/zimbra/ssl/zimbra.$(date "+%Y%m%d")'
echo "複製憑證到 zimbra 認可目錄下" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
cp /opt/zimbra/ssl/letsencrypt/privkey.pem /opt/zimbra/ssl/zimbra/commercial/commercial.key
chown zimbra:zimbra /opt/zimbra/ssl/zimbra/commercial/commercial.key
echo "開始部署憑證" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
su zimbra -c 'cd /opt/zimbra/ssl/letsencrypt/ && /opt/zimbra/bin/zmcertmgr deploycrt comm cert.pem fullchain.pem' >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
echo "重啟 zimbra 服務" >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt
su - zimbra -c 'zmcontrol restart' >>$BACK_DIR/ssl_LOG${DATE_TODAY}.txt